Zeusbot
Trojan horse malware that is often used to steal banking information by website monitoring and keylogging.

Memory Image
Download the memory image containing Zeus malware from the below repo and unzip it.
unzip ~/Downloads/zeus.vmem.zip
Identifying the profile
As usual, we’ll start by identifying the profile of the image using
imageinfoplugin.
python2 vol.py -f zeus.vmem imageinfo

We’ll select “WinXPSP2x86” from the suggested profiles and continue.
Enumerating Processes
Now that we have identified the profile of the memory image, we can start to look for suspicious activities by first listing down the processes using
psscan.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 psscan

We don’t see anything suspicious from the processes listed here as the count and names of the processes look fine.
We can try
pstreeplugin to look at the parent-child relationship.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 pstree
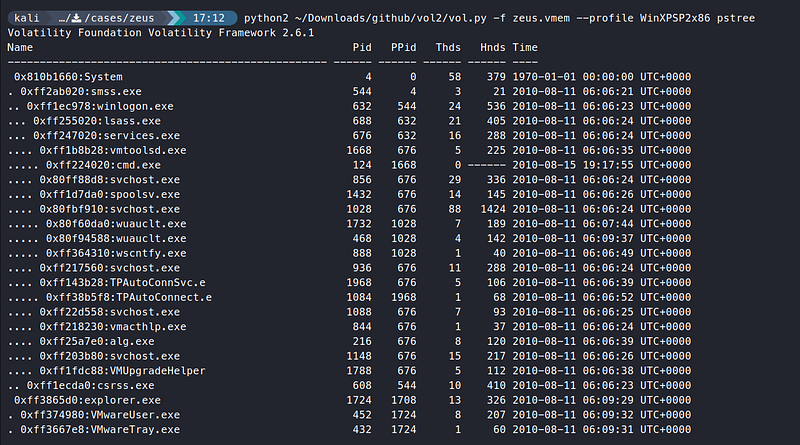
Still we don’t find anything suspicious here.
So the names of the processes, count and parent-child relationship all look benign till now.
Network connections
Another best place to look for suspicious activities is the network connections that the malicious process might have made to their Command and Control (C2) servers.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 connections
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 connscan

Though there are no open connections shown by
connectionsplugin,connscanshows that there are connections made by the PID “856”.Let’s check the reputation of the IP address listed here using VirusTotal.

It does look suspicious. Let’s look into this further.
Also, look at the other sections of the result page in VirusTotal and see if you can add to your suspicion about the IP address (like country details, files it is communicating and referring to).
Malicious Process
Now let’s see which process was communicating with this IP address by grepping the output of
psscan.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 psscan | grep 856

We can see that the process that made the suspicious network connection is “svchost.exe” of PID 856.
Now let’s look at the path of the executable using the
cmdlineplugin.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 cmdline -p 856

We don’t get anything from here, as the path of the process looks legit.
Code injection
Till now nothing about the process looks suspicious. Maybe the code is injected into this process.
To investigate this, let’s use
malfindplugin.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 malfind -p 856

We can see that this process has
MZheader and protection ofPAGE_EXECUTE_READWRITE, which means that this memory region is marked as executable, and it can also be both read from and written to.This is unusual and suspicious because it allows an attacker to execute code from that memory region and also modify its content dynamically.
In legit scenarios, memory regions won’t be executable and writable at the same time.
Let’s dump this process using
procdumpand investigate it using VirusTotal.
mkdir procdump
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 procdump -p 856 -D procdump/
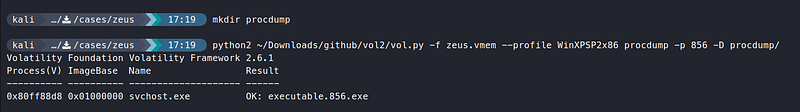
file procdump/executable.856.exe
sha256sum procdump/executable.856.exe

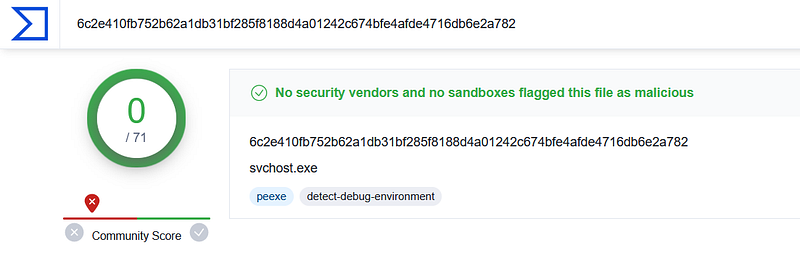
Interesting! It is not flagged as malicious.
But this result alone should not make us conclude that this is a legit process. In fact, we saw that this process had made suspicious network communications and also we suspect code injection. So let’s not stop here.
Let’s try dumping the region of memory where we think that the malicious code is injected and analyze it. For this we can use the
vaddumpplugin and provide the PID, base address of the memory region that we suspect from the output ofmalfind.
mkdir vaddump
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 vaddump -p 856 -b 0xb70000 -D vaddump/
sha256sum vaddump/*


Alright! Our guess was not wrong. This memory region is indeed malicious confirming code injection.
Okay, now we have a process that has malicious code injected into it and is contacting an IP address that is flagged as malicious. Let’s investigate further and see if we can gather some more IOCs.
Persistence
Let’s try searching for persistence mechanisms that a malware commonly uses.
Some of the common registry keys that malwares use for persistence are Run, RunOnce keys, Winlogon keys, Startup keys, Services keys etc.
We can use a plugin called
winesapwhich will go through and list all the AutoStart Extensibility Points (ASEP). Link to the plugin here.But I went through the keys one by one using the
printkeyplugin.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 printkey -K “Microsoft\Windows\CurrentVersion\Run”
python2 vol.py -f zeus.vmem — profile WinXPSP2x86 printkey -K “Microsoft\Windows\CurrentVersion\RunOnce”
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 printkey -K “Microsoft\Windows NT\CurrentVersion\Winlogon”

In the “Userinit” value of the Winlogon key, we can see an unusual file “sdra64.exe” located in the system32 directory.
The “Userinit” value typically points to “userinit.exe”, which is responsible for initializing the user environment and loading the user profile during the logon process.
By adding the path to the existing Userinit value, it maintains persistence.
Malicious files
Let’s look further at the file by dumping it using the
dumpfilesplugin and investigating in VirusTotal.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 filescan | egrep -i sdra
Using
filescanplugin and grepping for the suspicious file name, we can obtain the physical offset of the file object, which we can provide todumpfiles.
mkdir filedump
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 dumpfiles -Q 0x00000000029d9b40 -D filedump/
sha256sum filedump/*
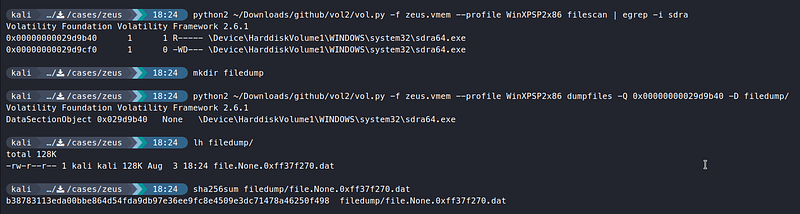

We can see that VirusTotal has flagged this file as malicious.
Another malicious process
If we look closely at the output of
filescan, the 3rd column displays the number “1”. This means that there is 1 handle to that malicious file object (which is malicious as we confirmed now).It’d be interesting to know which process has a handle to this malicious file. We can find this out using the
handlesplugin and grepping for the malicious file.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 handles | egrep -i sdra
We can see that the PID 632 has a handle to the file “sdra64.exe”. Grepping for that PID from the output of
psscan, we can see that this process is “winlogon.exe”.
python2 vol.py -f zeus.vmem — profile WinXPSP2x86 psscan | egrep 632

Now we see another process that might have injected code in it. Let’s dig in further.
python2 vol.py -f zeus.vmem —profile WinXPSP2x86 malfind -p 632

Using
malfindplugin, we can see the memory region withMZheader and withPAGE_EXECUTE_READWRITEprotection. This definitely does not look good.Let’s dump the process and look for it in VirusTotal.
python2 vol.py -f zeus.vmem — profile WinXPSP2x86 procdump -p 632 -D procdump/
sha256sum procdump/executable.632.exe

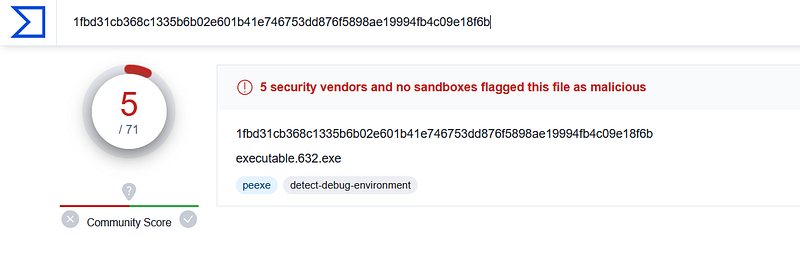
VirusTotal flags this as malicious and now we have another malicious process.
Mutual exclusions
Since we have multiple malicious processes, we can look for Mutexes that the malware might have created to ensure that only one instance of it is running at a time.
We can use the
handlesplugin, specifying the object type asMutantand providing the PID.
python2 vol.py -f zeus.vmem — profile WinXPSP2x86 handles -t Mutant -p 632

From the output, the Mutant “_AVIRA_2109” looks suspicious by its naming pattern and searching for it online, we can confirm it.
I thought it’d be interesting to also look at the handles of “svchost.exe” for any mutex and indeed it has one similar mutex named “_AVIRA_2108”
python2 vol.py -f zeus.vmem — profile WinXPSP2x86 handles -t Mutant -p 856

Now that we have gathered some IOCs, let’s start listing them down.
Indicators of Compromise (IOCs)
The presence of Zeus or Zbot can be identified with the help of the below IOCs.
C2 connection
193.104.41.75
Processes with injected code
svchost.exe
winlogon.exe
Registry entry
Key: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon Value: Userinit Data: C:\WINDOWS\system32\sdra64.exe
File
Name: sdra64.exe Path: C:\WINDOWS\system32\sdra64.exe Hash: b38783113eda00bbe864d54fda9db97e36ee9fc8e4509e3dc71478a46250f498
Mutexes
_AVIRA_2109
_AVIRA_2108
Summary
We analyzed the memory dump containing Zeus/Zbot malware using the Volatility framework. We identified a suspicious network connection made by a “svchost.exe” process which had malicious code injected into it. Then we found a file named “sdra64.exe” used for persistence and it had a handle to “winlogon.exe” which also had malicious code injected into it. Finally, we found some Mutexes used by these processes and listed down the IOCs.
If you like my work, consider supporting me: BuyMeACoffee
Last updated